Add your feed to SetSticker.com! Promote your sites and attract more customers. It costs only 100 EUROS per YEAR.
Pleasant surprises on every page! Discover new articles, displayed randomly throughout the site. Interesting content, always a click away
armadillo
Armadillo Managed Services helps you to embed security as a core part of your business development strategy by focusing on your security fundamentals.Armadillo Managed Services Partners with Tanium to Provide Complete Control and Visibility of Endpoints 1 Jan 2024, 5:27 pm
United Kingdom – January 1st 2024
Armadillo Managed Services today announces a strategic partnership with Tanium, the industry’s leading provider of Converged Endpoint Management (XEM). The two organisations will combine expertise to help organisations protect business-critical assets.
The collaboration delivers comprehensive managed services that protect every endpoint from cyber threats by integrating workflows across IT, Risk, Compliance, and Security. Armadillo Managed Services will leverage the full breadth of the Tanium XEM platform, enhancing support for both enterprise and mid-market organisations across Europe.
By combining the technical capabilities of Tanium with Armadillo’s 22 years of experience delivering endpoint solutions, security and IT operations teams can access valuable insights into their IT infrastructure which helps to identify vulnerabilities and then fix them rapidly. As a proud member of the Tanium partner ecosystem, Armadillo Managed Services integrates its Endpoint Protection (EPP) capabilities with the Tanium XEM platform.
“We have built a Tanium powered managed service, enhanced by Armadillo’s white glove customer support,” said Mark Newns, CEO of Armadillo Managed Services. “This is delivered by our Tanium-trained engineering team and enables us to offer this unique offering to the market, which is gaining traction already amongst our customers.”
“A cornerstone of our growth and commitment to delivering a truly valuable solution hinges on our partners,” said Stuart Robson-Frisby, RVP of EMEA Channels at Tanium. “Our alliance with Armadillo Managed Services is a step towards dismantling the barriers that often arise between cybersecurity and IT operations teams. Together, we are delivering a platform that provides these teams with access to a single source of truth about their IT environment. This significantly improves security and increases efficiency for resource strapped internal teams.”
Armadillo’s vision is to establish a Centre of Excellence, rooted in Tanium’s advanced capabilities, covering the spectrum from initial discovery to Business-as-Usual (BAU) operations. This Centre will not only bolster Armadillo’s position as a leader in the field but also reaffirm the company’s commitment to elevating the standards of IT management and security across Europe.
The post Armadillo Managed Services Partners with Tanium to Provide Complete Control and Visibility of Endpoints appeared first on armadillo.
Don’t Let Ransomware Halt Your Business 17 Nov 2023, 7:15 am
Are your endpoints protected?
Endpoints are any devices that individuals and organisations use to access and interact with network resources and data. These include (but are not limited to):
- Desktop computers
- Laptops/tablets
- Smartphones
- Servers
Given their critical role, securing endpoints is paramount to maintaining the overall security of your organisation’s network. They have become primary targets of cyber-attacks because they provide attackers with entry points into networks, steal sensitive information, or disrupt operations.
What is endpoint protection?
Endpoint protection, also known as endpoint security, refers to the strategy and set of tools and technologies designed to secure and protect an organisations’ endpoints from possible threats. These threats can include malware, viruses, ransomware, phishing attacks, zero-day exploits, and other types of malicious activities.
Solutions can be deployed on individual devices, managed centrally by an IT department, or provided as a cloud-based service. The goal is to create a multi-layered defence system that combines prevention, detection, and response mechanisms to protect endpoints from whatever threat that may occur.
It can just take a single device to be compromised and lead to data breaches, data loss, and disruptions in business operations. Are you confident every smartphone, tablet, and laptop in your organisation is safe, and not an open door for an attacker?
Protecting your endpoints with Artificial Intelligence (AI)
Using AI for endpoint protection has become increasingly popular and effective in the cybersecurity field. AI-powered endpoint protection solutions help to leverage algorithms and other techniques to enhance threat detection, response, and overall security.
Deep learning is an advanced branch of AI and is inspired by the brain’s ability to learn. Once a brain learns to identify and object, its identification becomes second nature. This is the same for deep learning. The computer is learning, not just memorising or following repetitive instructions, but looking at something it doesn’t know and truly learning all about it, without human interaction.
When applied to cybersecurity, and more specifically preventing endpoint protection, it uses neural networks to instinctively and autonomously predict threats to stop unknown malware and zero-day attacks by identifying and preventing them before they can execute and enter an environment.
Deep Instinct’s zero-day approach to Endpoint protection
From the moment malware executes on the endpoint, it’s a race against time to stop it. Traditional security solutions struggle to detect and respond quickly to unknown threats, taking minutes, hours, or even days — during which time the malware has succeeded, and your environment is compromised.
Deep Instinct’s Prevention for Endpoints product takes a proactive approach to improve your overall endpoint security effectiveness and efficiency to reduce risk and lower overall TCO (total cost of ownership). With a uniquely architected deep learning based solution they prevent over 99% of unknown zero-day threats, in less than 20m milliseconds.
Deep Instinct has pioneered the use of deep learning in cybersecurity to prevent known and unknown malware, zero-day exploits, ransomware, and common script-based attacks for the broadest range of file types, faster and with less than 0.1% false positives – saving your security teams’ valuable time!
The post Don’t Let Ransomware Halt Your Business appeared first on armadillo.
29 Mar 2023, 4:06 pm
Join Daniel Oxley and Hannah Farrer as they discuss how you can regain complete visibility of your entire estate, from all your managed devices through to the unknown or unmanageable ones. You need a single source of truth for your estate, starting with full discovery. Once you are in possession of this detail, we will teach you how best to improve your processes whilst mitigating your risks.”
Do you know your risk score?
Start scoring your endpoints against dozens of risk and attack vectors, such as vulnerabilities, threats, compliance, patching, sensitive data, in 5 days at zero cost and minimal effort. Be proactive in your endpoint management rather than reactive, starting with a comprehensive view of your entire environment and risk posture.
The Armadillo Risk Assessment Programme provides dynamic scoring for each endpoint against multiple vectors as well as an actionable improvement and remediation plan.
We have now enhanced our offering to include Armadillo’s ‘Cyber Risk Assessment Programme’ which will give you a real time view of the entire environment. Contact hfarrer@wearearmadillo.com to find out more.
The post appeared first on armadillo.
On -Demand Live Attack Simulation 27 Feb 2023, 5:21 pm

Check out our on-demand recording of our Live Attack Simulation we hosted with Cybereason

The post <span class="yellow"> On -Demand </span> Live Attack Simulation appeared first on armadillo.
Configure, Validate, Remediate, and stay Compliant. 17 Oct 2022, 9:58 am
80% of ransomware attacks are rooted in mistakes made by a business in configuration, according to a recent article by Microsoft. Think about that for a moment: four fifths of all the damage caused by ransomware to businesses over the last few years could quite possibly have been cleanly avoided without anything more than having the correct configuration being in place. I recognise that this is an easy statement to make, and it is headline grabbing as well, but stay with me.
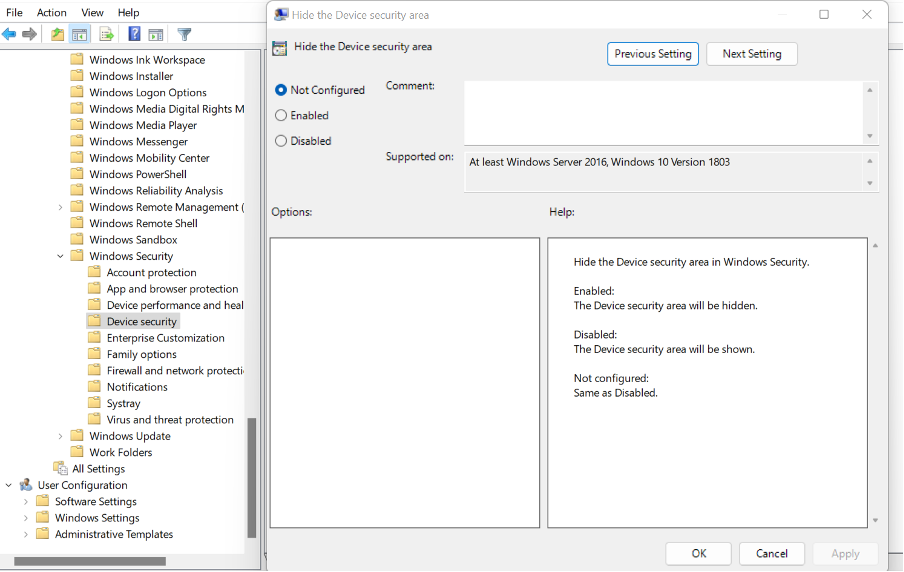
Typically, certainly in the case of most Microsoft products and services, you use Active Directory Group Policy Objects (GPO) to deploy and manage configuration on your managed devices, be it the user experience, device behaviour or security configuration. But GPO isn’t actually very good at what it tries to do, sure it is from the product vendor and forms the best way to maintain a common and approved configuration, but it is also slow, hard to troubleshoot, cryptic with double negatives in the descriptions, has no true reporting or feedback, and can only be used in well-connected environments. It has always had shortcomings and quirks, but primarily it was never designed for the world of WFH, BYOD, VPN, ZTNA or any other of the initialisms that we use every day.
My personal pet hate with enforcing configuration via GPO is the way that you set a configuration into policy and must cross your fingers and hope that: a) it has been applied to every targeted device – and only those devices that are intended and, b) the policy item remains enforced permanently. This leads to a potential scenario where a policy item was not applied or it was subsequently circumvented or removed, and this outcome can leave your environment wide open to risk as it only takes 1 incorrectly configured device to leave your environment exposed.
But love it or hate it, GPO is here to stay, and it is not going to change anytime soon.
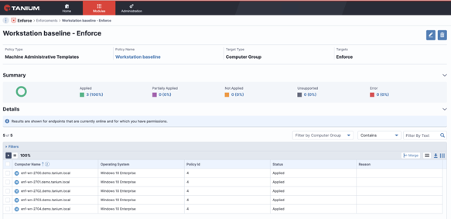
When Tanium released their Enforce module, I was excited with the ability to finally apply policy, see where policy failed to apply or where it was circumvented, and also apply the policies items across all devices globally with no need to follow Active Directory hierarchy – all in real-time. It changed the way that policy is managed and deployed across an environment.
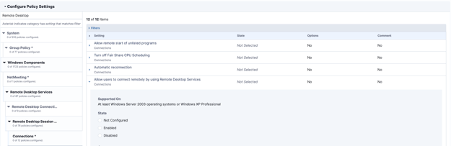
With Enforce you can configure all machines policy, combined with your disk encryption and Windows Defender policy, from a single console and then immediately apply it to all managed devices, where they are on-premise, off-premise, cloud, hosted, datacentre, or even across all devices regardless of whether or not they are in the same Active Directory Domain/Forest; it is truly centralised policy management. And because of the real-time nature of the Tanium platform, you finally have that visibility that was missing. Whilst it is not perfect, Enforce is a superb solution to this problem, and when compared with the other facets on the Tanium platform it is a solution that is very hard to disregard.
But what about misconfigurations? What about the devices where policy was applied, but it wasn’t the correct configuration, or doesn’t map to a best practice? In this scenario your policy is working just fine, the problem instead is that the wrong configuration is being deployed, and once again you have no idea that this situation even exists until something happens.
In my opinion a misconfiguration is so much worse than no configuration because with a misconfiguration you can led to believe that you are protected whilst blissfully unaware that there is an exploitable vulnerability in your network; it’s a false sense of security in a dangerous world. And this leads back to my opening sentence in this post, that 80% of all ransomware events were due to misconfigurations.
The answer to this quandary already exists, I am not hypothesising about a gap in the tech industry that leaves businesses wide open and vulnerable, and with no solutions available; this 80% ransomware scenario of misconfiguration that I describe can be addressed today, and with minimal effort.
The answer to this quandary already exists, I am not hypothesising about a gap in the tech industry that leaves businesses wide open and vulnerable, and with no solutions available; this 80% ransomware scenario of misconfiguration that I describe can be addressed today, and with minimal effort.
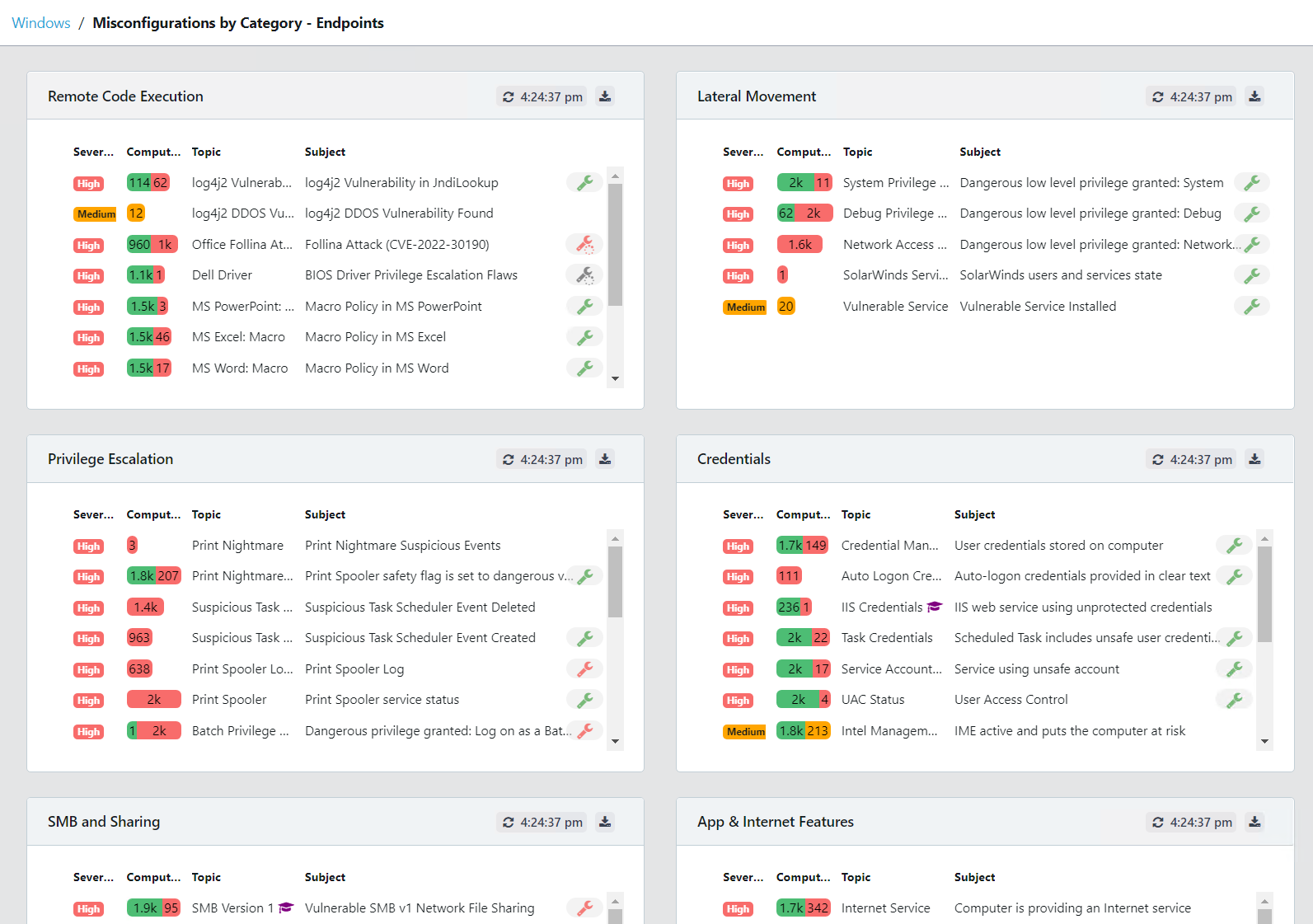
Microsoft for Startups Tom Davis recently described GYTPOL as “one of the most exciting cyber-startups I have come across in recent years”, and I could not agree more. It is a solution that can answer all the points I made above, more. With GYTPOL, as you apply policy across your environment it is inspecting it to make sure that it is applied to a device, and importantly that the configurations deployed are correct and that they match best practices, standards, recommendations, and everything else. And not only that, but they have also taken the “big button” approach to make remediation immediate and easy; you don’t need to go back and trawl through settings, layers of policy or anything else, you just hit the button for an immediate response.
Take a look at the screenshots in the gallery below, I have taken these from the Armadillo test lab. You can see the reporting, the detail for any alert, and how to fix it. What impresses me the most without doubt is the reporting and dashboards because, from a single screen, I can see how big a problem I have, what the problems are, where they are, and how they map to the CIS benchmark.
Put it on your to-do list right now: this is a problem lurking in every single IT environment and goes overlooked, understated, and unaddressed. But not addressing it puts your business in that 80% bracket, which can be very expensive to recover from.

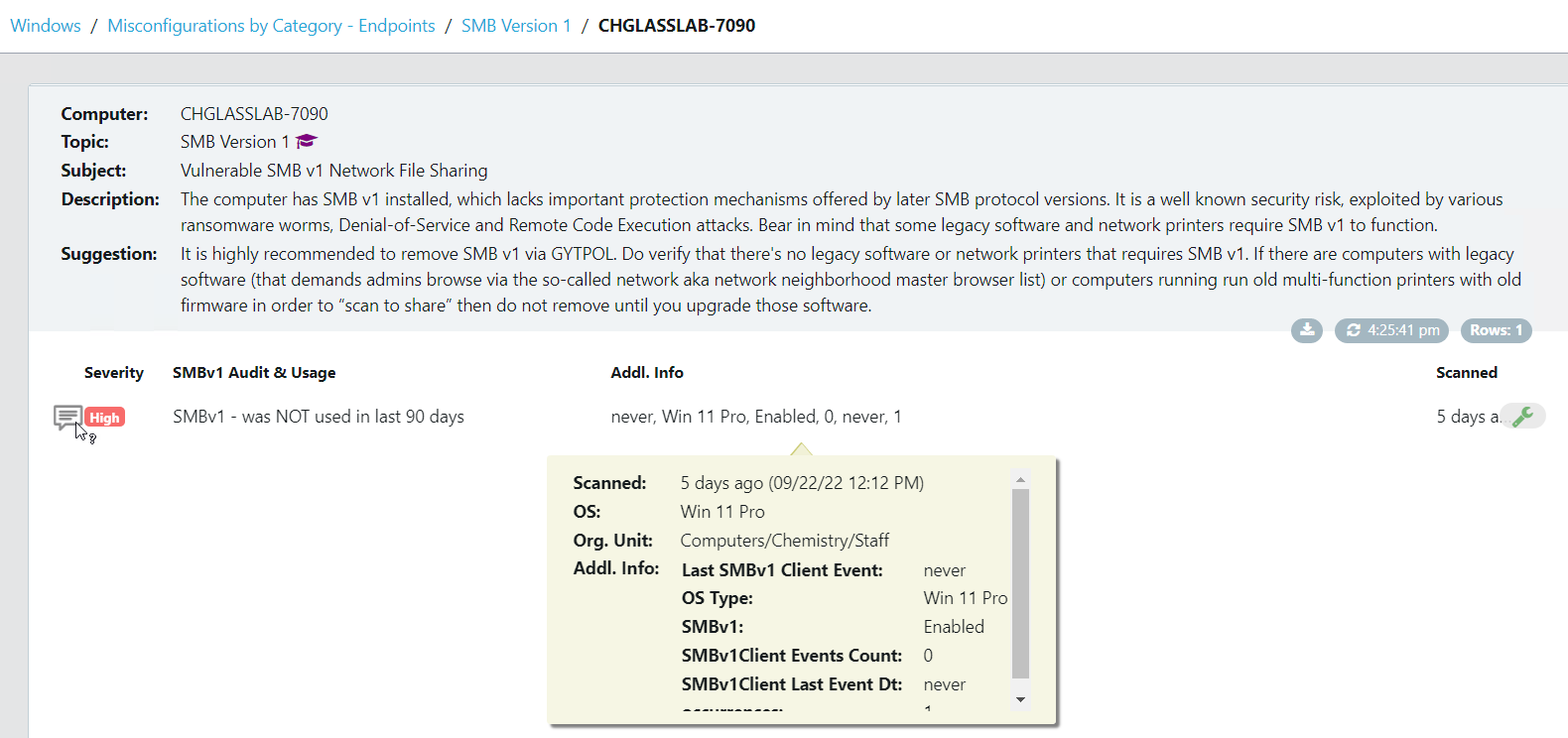
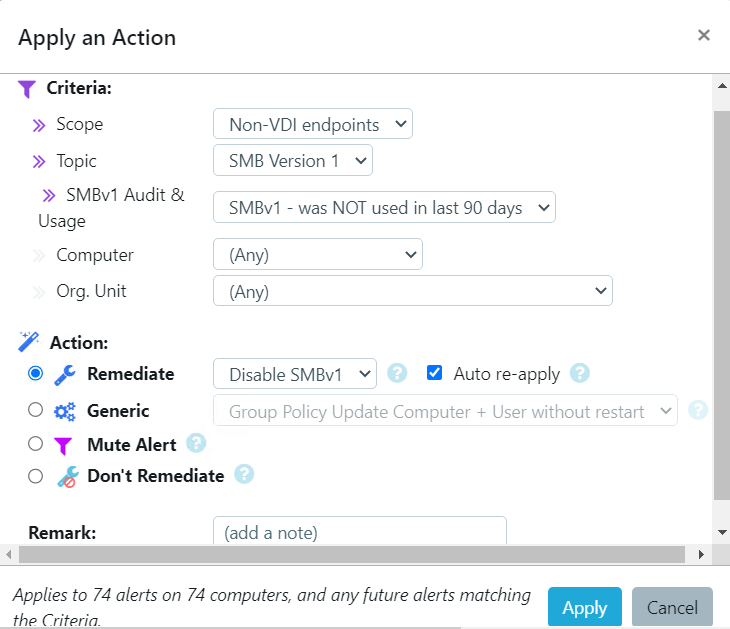
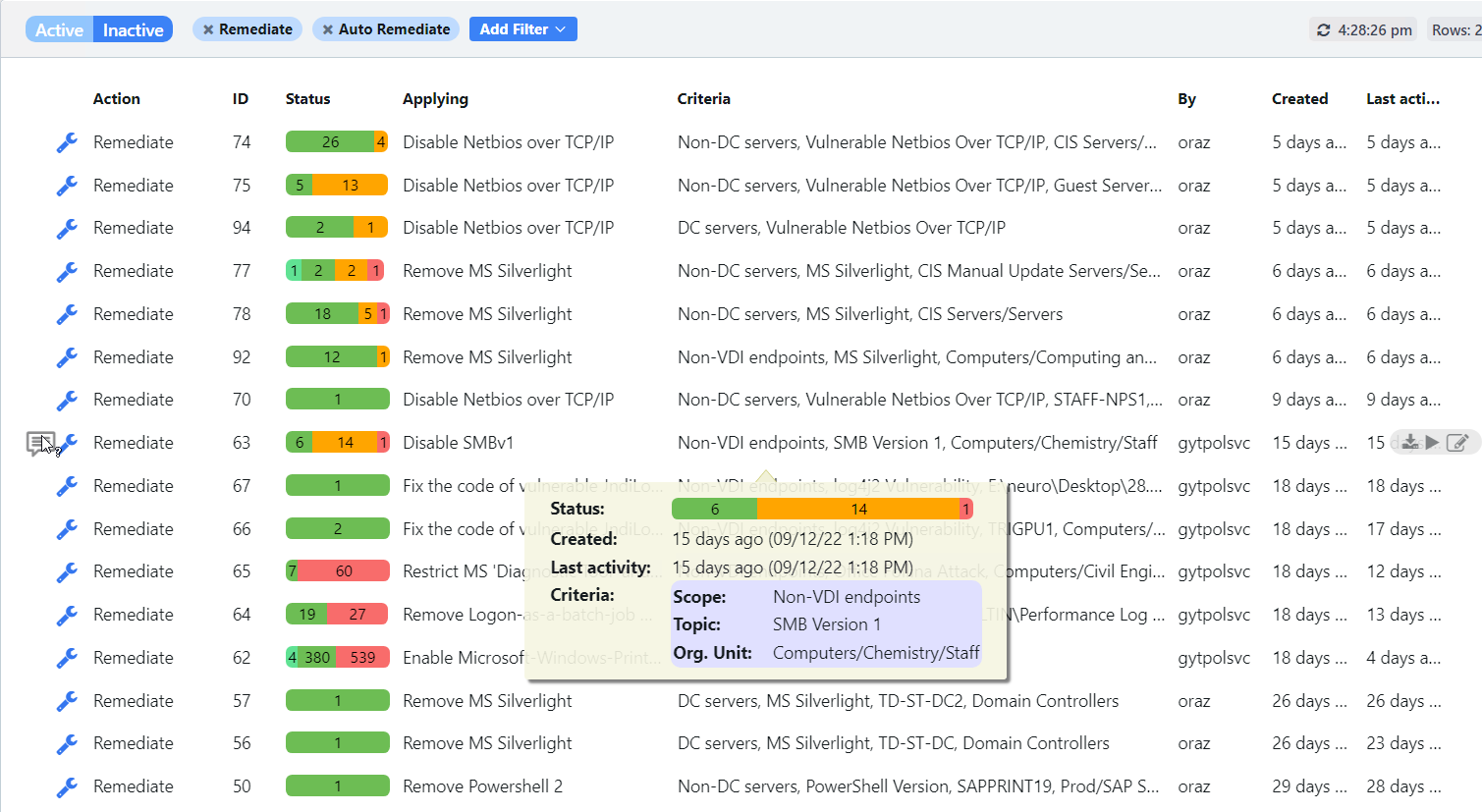
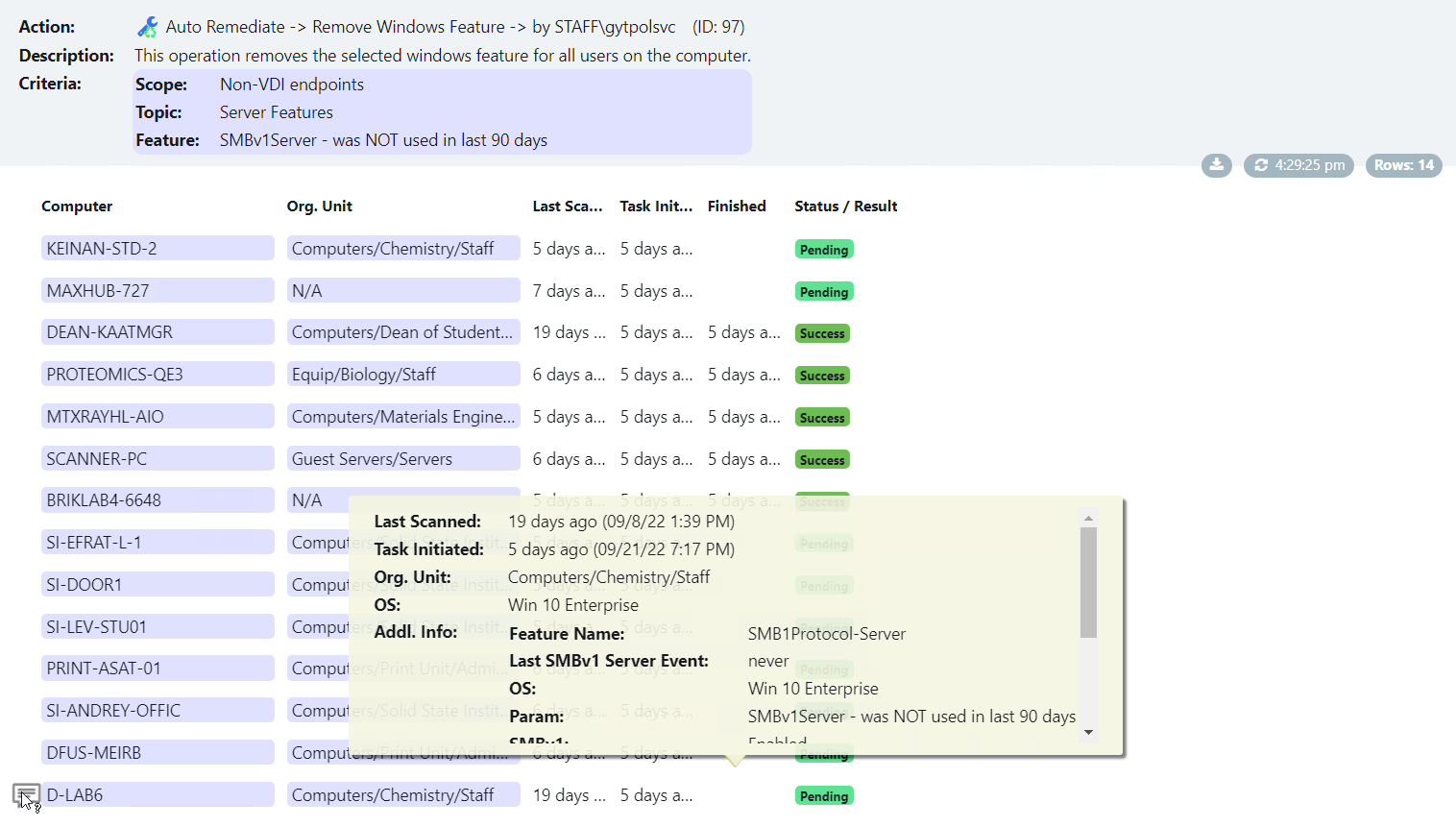
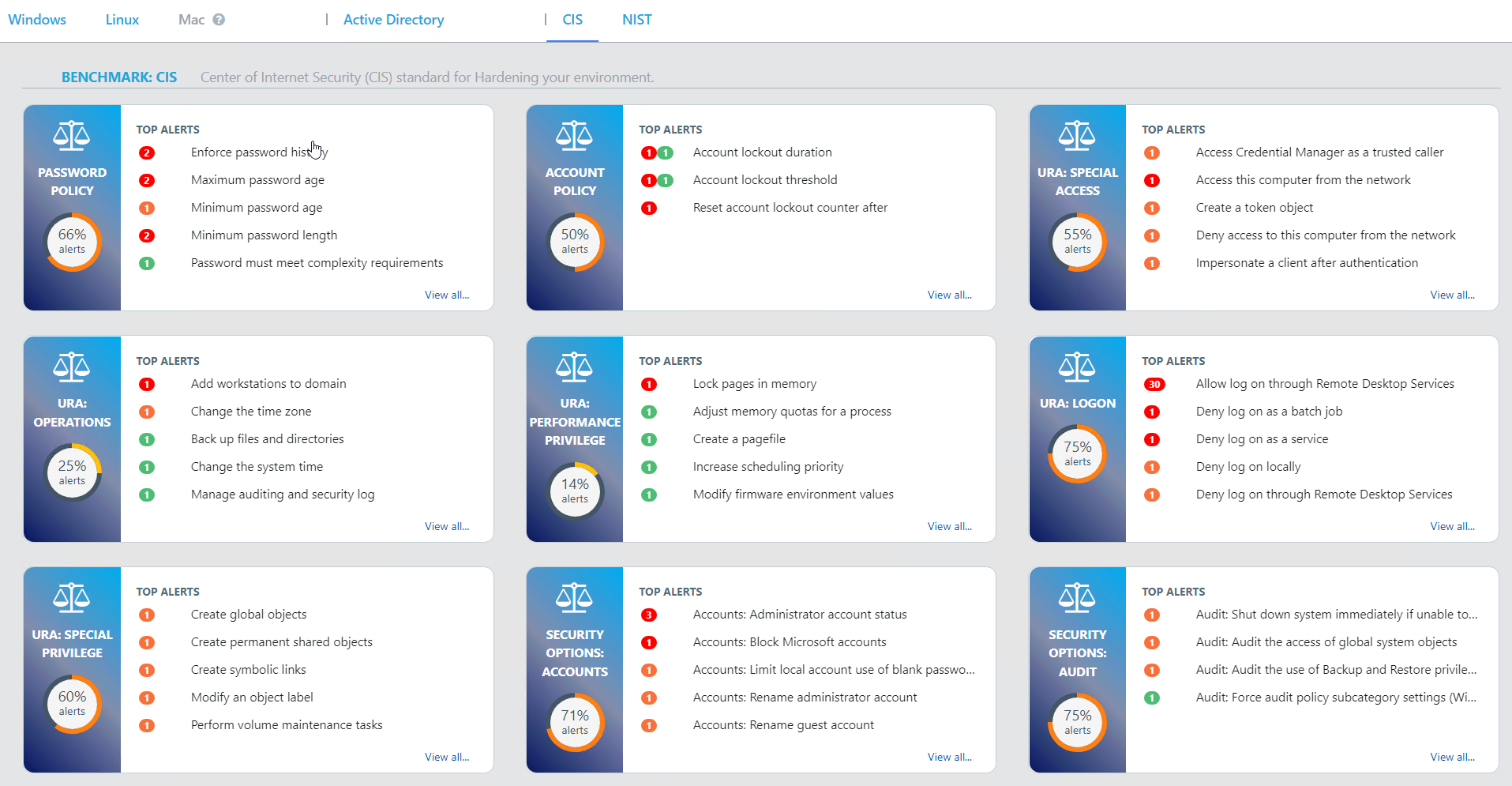
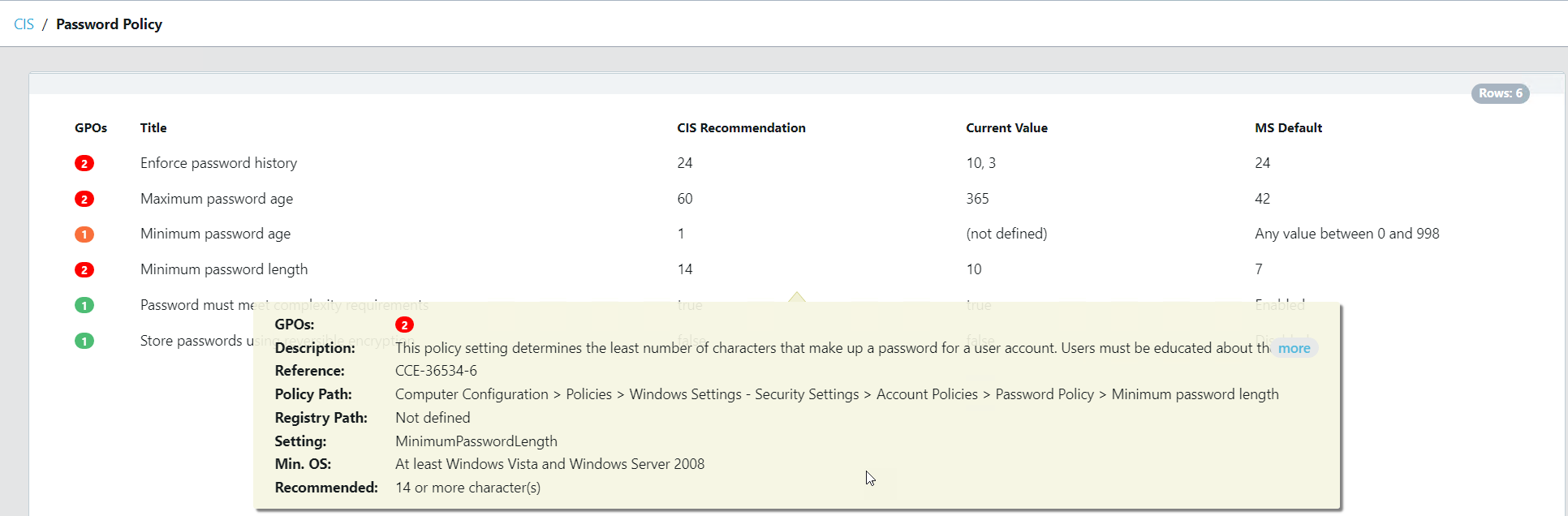
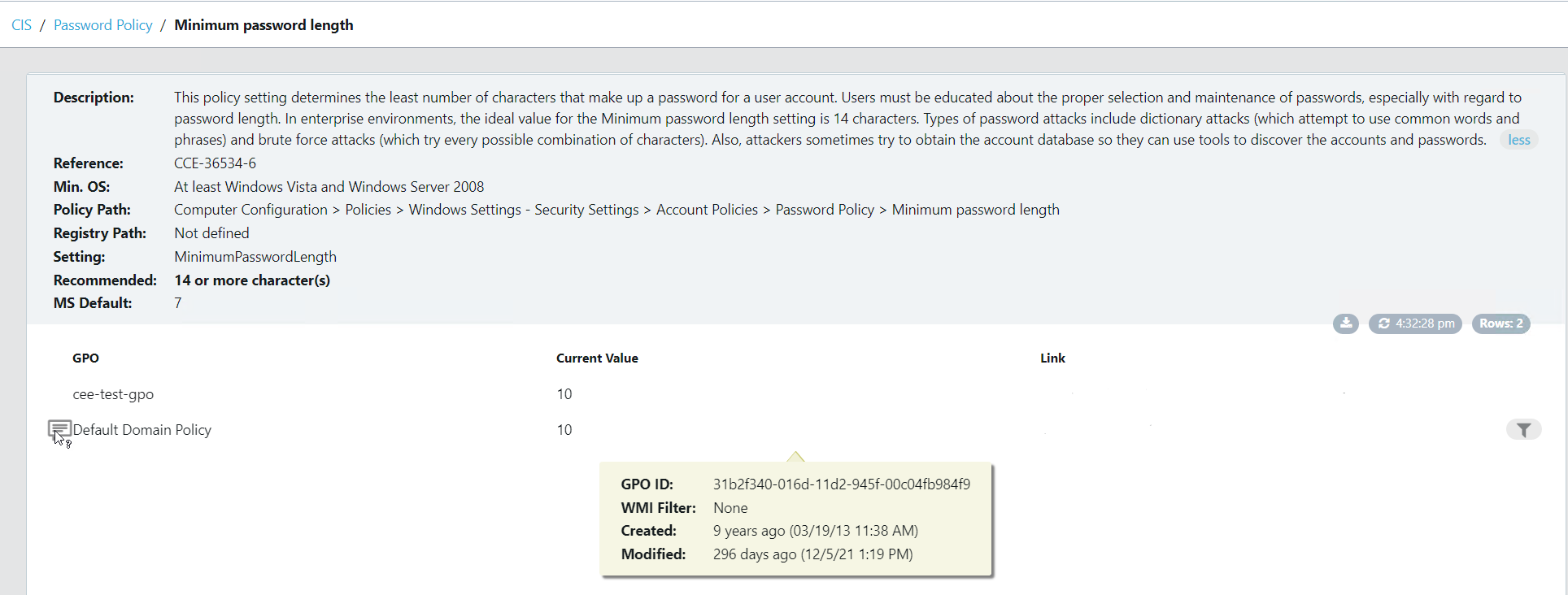
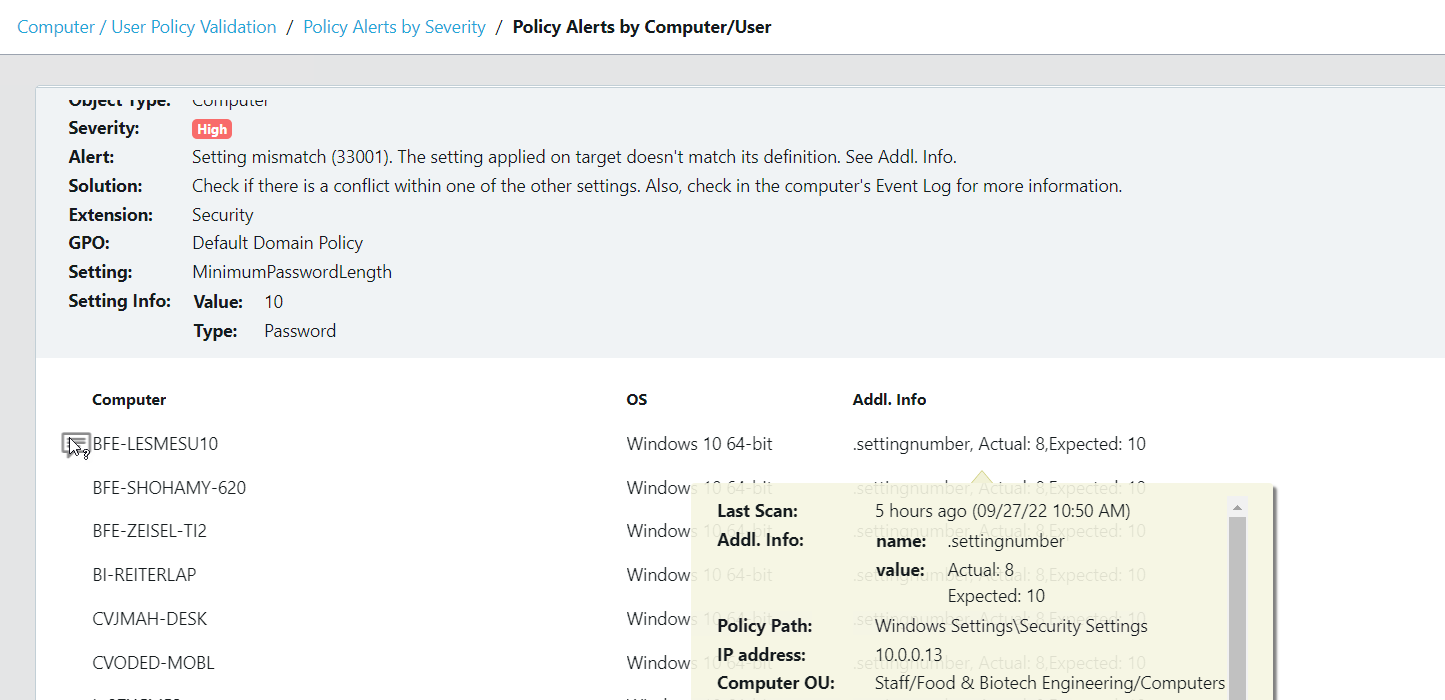
The post Configure, Validate, Remediate, and stay Compliant. appeared first on armadillo.
Armadillo Managed Services partner with Venari to raise the curtain on encrypted traffic. 12 Oct 2022, 2:50 pm

London, September 28th 2022 – Armadillo Managed Services are pleased to announce its new strategic partnership with Venari Security, a London-based cybersecurity company, who provide organisations with visibility and insight into their encrypted attack surface and how encryption is actively used across their enterprise, providing a level of context previously unattainable.
Armadillo integrates Venari Security’s pioneering Encrypted Traffic Analysis (ETA) platform into its existing portfolio, enabling organisations to identify attackers in encrypted traffic and monitoring for any deviation or change. The platform uses a unique combination of artificial intelligence (AI), machine learning (ML), behavioural analytics and a proprietary rules engine to provide actionable intelligence and detect potential threats, in real time. The technology provides insight and visibility into how encryption is actively used across the enterprise. This means businesses can better maintain strong encryption standards, by ensuring internal and regulatory compliance whilst supporting data privacy in transit. Ultimately, enterprises can conduct their business in confidence and minimise the risk of a security attack.
Armadillo Managed Services are able to consult on resilient cyber security that improves a business’s ability to detect, withstand and respond to security attacks, and this new partnership further enhances this ability and the services offered. Focusing on three main practice areas, Armadillo supports businesses in agile cyber security strategy, support and services that work in tune with an organisation’s operations.
“Our partnership will enable Armadillo to widen the lens of enterprise security, empowering its customers to maintain strong encryption standards, whilst mitigating against malicious activity hidden within encrypted traffic on their networks,” said Hiten Mistry, CRO at Venari Security. “Together we will empower more businesses to focus on delivering added value for their customers and driving revenues, as they can be safe in the knowledge that disguised threat actors hidden within encrypted traffic can be stamped out before they make an impact.”
“We have been following the progress of Venari Security with great interest and are confident that our strong relationship with the Venari Management Security team will help drive the solution and our business forward.”, says Armadillo CEO Mark Newns.
About Venari Security
Headquartered in London, Venari Security is an award-winning cybersecurity SaaS provider with the purpose to make the encrypted world more secure and compliant. Our ETA (Encrypted Traffic Analysis) platform fundamentally changes the way encrypted traffic is analysed. Without decryption, the ETA platform identifies threats and suspicious behaviour while delivering internal and regulatory compliance. Venari Security uses machine learning, artificial intelligence, and behavioural analytics to accurately understand the abnormalities between normal and anomalous behaviour during which data remains private.
Phone:
+ 44 (0) 208 0888 222
Email: info@wearearmadillo.com
The post Armadillo Managed Services partner with Venari to raise the curtain on encrypted traffic. appeared first on armadillo.
Ultimate Secure Code Warrior Tournament: 2021 Edition 2 Apr 2021, 12:22 pm
DO YOU HAVE WHAT IT TAKES TO TAKE ON THE BEST DEVELOPERS IN THE INDUSTRY?
Join Armadillo and Secure Code Warrior in the Wild West where Developers see if they have the coding skills to take on security.
6th – 8th May 2021
Hosted by Secure Code Warrior you will take part in a series of vulnerable code challenges that ask you to identify a problem, locate insecure code, and fix a vulnerability. The tournament will allow you to compete against other participants so you can measure your secure coding skills and see if you’re the best of the best.
All challenges are based on a range of software languages including C Basic, C++ Basic, Perl Dancer2, Python Django, JavaScript Node.js (Express), JavaScript Angular.io (2+) and JavaScript React.
“You see, in this world, there’s two kinds of people, my friend; those with coding skills and those who don’t. You code” – The Good, the Bad and the Code.
How to Join the Tournament:
- Simply complete the contact form below and we will send information with the next steps and your tournament portal link to join, make sure to register beforehand.
- This tournament will be open from 6:00am Thursday 6th May and will close at 11:59pm on Saturday 8th May, entry to the tournament is free!
- The tournament is run virtually, and is web based so you can join through your laptop from the most convenient location and time.
PRIZES!
First place: Sony Wireless Headphones
Second and Third place: Secure Code Warrior Swag
First prize can only be shipped to a UK address. Players who go against the spirit of the competition may be removed. Prizes and participants may be limited at Armadillo’s discretion.
The post Ultimate Secure Code Warrior Tournament: <span class="yellow"> 2021 Edition </span> appeared first on armadillo.
C3M Press Release 2021 17 Feb 2021, 11:50 am

San Francisco, February 17th, 2021: C3M, the San Francisco based Cloud Security and Compliance vendor, today announced its partnership with the UK MSP Armadillo.
C3M, a leader in Cloud Security (CSPM) and Cloud Identity and Entitlement (CIEM) will be providing Armadillo and their clients with access to their industry leading platform, Cloud Control. Cloud Control provides a unified cloud security operations and management experience for all organisations who need to solve the growing security and compliance challenges for their public cloud infrastructure.
Armadillo CTO, Rob O’Connor, said, “The adoption rate of AWS, GCP and AZURE in our clients and the UK market as a whole was unprecedented in 2020 and whilst this move certainly allowed companies to function, rapid adoption of any technology can bring misconfigurations and security risks.
At Armadillo we go beyond cyber security and build cyber resilience for all of clients and therefore we felt it critical to launch (or bolster) our Cloud Security and Posture management service in 2021. We rigorously researched and tested the current vendors in this space and are delighted today to announce our partnership with C3M. We found Cloud Control is flexible, cloud vendor agnostic and easy to use platform on the market and today C3M is already successfully deployed in the world’s largest enterprises.
Our partnership with C3M will allow Armadillo to provide an array of Cloud Security Services from posture assessments through to a fully managed service.
Paddy Viswanathan, Founder and CEO at C3M, said: “‘We are delighted to have appointed Armadillo for the UK Market. The Armadillo team exude experience and desire to ensure they are delivering top notch cloud security solutions to their clients and the market as a whole.
________________________________________________________________
About C3M
C3M, LLC is a San Francisco headquartered Cloud Security solutions provider. C3M’s Cloud Control is a 100% Agent-less, API based, cloud-native security solution that offers organisations complete cloud control through automated security intelligence, giving them actionable insights into the cloud, its security, and infrastructure, while also auto-remediating any security violations it detects. C3M Access Control helps enterprises gain complete control over identities and infrastructure entitlements, and right size identity privileges.
www.c3m.io
About Armadillo
Formed in 2001, Armadillo is one of the UK’s most experienced cyber security specialists, focusing on enabling businesses to conduct their business in confidence, without fear of security attack and without compromising how they operate.
www.wearearmadillo.com
Phone:
+ 44 (0) 208 0888 222
Email: info@wearearmadillo.com
___
San Francisco, February 17th, 2021: C3M, the San Francisco based Cloud Security and Compliance vendor, today announced its partnership with the UK MSP Armadillo.
C3M, a leader in Cloud Security (CSPM) and Cloud Identity and Entitlement (CIEM) will be providing Armadillo and their clients with access to their industry leading platform, Cloud Control. Cloud Control provides a unified cloud security operations and management experience for all organisations who need to solve the growing security and compliance challenges for their public cloud infrastructure.
Armadillo CTO, Rob O’Connor, said, “The adoption rate of AWS, GCP and AZURE in our clients and the UK market as a whole was unprecedented in 2020 and whilst this move certainly allowed companies to function, rapid adoption of any technology can bring misconfigurations and security risks.
At Armadillo we go beyond cyber security and build cyber resilience for all of clients and therefore we felt it critical to launch (or bolster) our Cloud Security and Posture management service in 2021. We rigorously researched and tested the current vendors in this space and are delighted today to announce our partnership with C3M. We found Cloud Control is flexible, cloud vendor agnostic and easy to use platform on the market and today C3M is already successfully deployed in the world’s largest enterprises.
Our partnership with C3M will allow Armadillo to provide an array of Cloud Security Services from posture assessments through to a fully managed service.
Paddy Viswanathan, Founder and CEO at C3M, said: “‘We are delighted to have appointed Armadillo for the UK Market. The Armadillo team exude experience and desire to ensure they are delivering top notch cloud security solutions to their clients and the market as a whole.
________________________________________________________________
About C3M
C3M, LLC is a San Francisco headquartered Cloud Security solutions provider. C3M’s Cloud Control is a 100% Agent-less, API based, cloud-native security solution that offers organisations complete cloud control through automated security intelligence, giving them actionable insights into the cloud, its security, and infrastructure, while also auto-remediating any security violations it detects. C3M Access Control helps enterprises gain complete control over identities and infrastructure entitlements, and right size identity privileges.
www.c3m.io
About Armadillo
Formed in 2001, Armadillo is one of the UK’s most experienced cyber security specialists, focusing on enabling businesses to conduct their business in confidence, without fear of security attack and without compromising how they operate.
www.wearearmadillo.com
Phone:
+ 44 (0) 208 0888 222
Email: info@wearearmadillo.com
___
The post <span class="yellow"> C3M </span> Press Release 2021 appeared first on armadillo.
Live Attack Simulation with Cybereason 6 Oct 2020, 2:35 pm

Thursday, 15th October 2020, 10:00-11:00am BST
Today’s attackers are able to translate a successful phish into persistent, stealthy network compromise. How does this happen, and what can we do to stop it?
In this special attack simulation, get an inside look at how multi-stage attack campaigns operate today. You will witness the attacker’s infiltration and watch the malicious operation as it moves across the entire environment. See the many opportunities an attacker has to advance the operation, and the ways a defender can break the kill chain and end the attack before crown jewels are compromised.
In today’s reality where prevention measures aren’t always enough and penetration can seem inevitable, we — the defenders — need to out think, outpace, and quickly end even the most sophisticated attack.

Why Should You Attend
You’ll come away with new knowledge on today’s attack campaigns and insights on how defenders can gain the upper hand. The session will share the attacker’s mindset and how it impacts our strategies as defenders.
Who Should Attend
Anyone responsible for protecting their organisation from attacks. From the CISO to the security architect and SOC analyst.
About the Speakers
Rob O’Connor has been working in cybersecurity for over 15 years as an end-user, a systems-integrator, a vendor, a reseller, and a managed service provider. As CTO at Armadillo Managed Services, he is responsible for identifying and bringing innovative technologies to his clients. Rob holds the CCIE Emeritus and CISSP certifications and an MBA in Technology Management (with distinction). He is a member of the Institute of Engineering and Technology and is a Chartered IT Professional.
Pavel Mucha is a Senior Pre-Sales Specialist at Cybereason and one of the good guys working tirelessly to give our customers the upper hand against adversaries. His experience with Cybereason and McAfee makes him a valuable asset for anybody needing to understand how to defend their organisation against the next generation of cyber threats.
The post <span class="yellow"> Live Attack Simulation </span> with Cybereason appeared first on armadillo.
ColorTokens Press Release 2020 26 Jun 2020, 8:53 am

We are partnering with ColorTokens to distribute the Spectrum Platform to our customers across the UK!
Click here to read the full announcement
________________________________________________________________

Please join our CTO Rob O’Connor and ColorTokens experts on July 28th at 11:00 a.m. – 12:00 p.m. BST for a webinar to learn how greater visibility unleashes the full potential of micro-segmentation, along with a live-in-action demonstration of this award-winning approach.
Register here to attend this session.
The post <span class="yellow"> ColorTokens </span> Press Release 2020 appeared first on armadillo.