Add your feed to SetSticker.com! Promote your sites and attract more customers. It costs only 100 EUROS per YEAR.
Pleasant surprises on every page! Discover new articles, displayed randomly throughout the site. Interesting content, always a click away
Mining the alphabet soup for what matters part 2 16 Mar 2021, 4:19 pm
NETWORK SECURITY: MINING THE ALPHABET SOUP FOR WHAT MATTERS |
On a theoretical level, it’s pretty easy to understand the value that WatchGuard’s layered UTM solutions provide, but analytical, scientific-minded people require quantifiable proof before they believe in any theory. Fortunately, NSS Labs, one of the world’s leading independent security product testing laboratories, has recently released a new threat warning service and testing methodology that proves the value of layered UTM security.
NSS Labs’ Cyber Advanced Warning System (CAWS) enables vendors and end-users alike to view how effectively a variety of network security solutions are blocking real-time security threats. The system enables subscribers to view the efficacy of different solutions operating under different profiles: the base profile only enables specific so-called NGFW features as defined earlier in this blog, as well as the advanced profile, where a vendor can enable value-added UTM services such as I described in the example above, and which we provide at WatchGuard.
WatchGuard has actively participated in the CAWS service for the past few months, and it not only has helped us increase our security efficacy, but has also provided a very quantifiably measure of why UTM defenses works. Here’s a chart showing WatchGuard’s “block rate” results for about a month of new CAWS attacks:
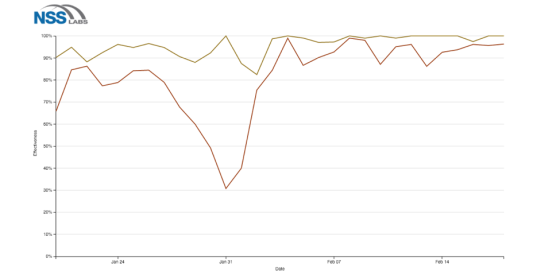
Figure 1: Image courtesy of NSS Labs CAWS system
In the chart above, the lower, orange line represents a traditional NGFW, that primarily only uses IPS to catch threats. However, the upper, muddy-yellow line represents our product using the full UTM feature set, which includes antimalware services like GAV and APT Blocker, as well as all our URL filtering services.
What’s important to note is the drop in our IPS only block rate during January 31st. While there could be a few reasons for this, it’s typically indicative of a new attack that our IPS didn’t catch. So why would I highlight this IPS miss? Well, looks at the yellow, UTM line… its block rate stays relatively high, despite the fact that IPS might have temporarily missed something new. Whether or not our daily IPS efficacy goes up or down, our full UTM defenses still catch well over 90% of the new threats each day, this further reinforces the importance of a layered approach to security as dips in IPS efficacy is not unique to WatchGuard.
Some have claimed, defense-in-depth, or layered security is dead. They make this declaration out of frustration, because lately we’ve seen so many organizations get compromised despite some defenses. However, I believe layered security is still the most effective way to prevent the majority of attacks. Breaches will still happen because no defense is infallible, but WatchGuard’s NSS Labs’ CAWS testing proves that having the layered security of a UTM appliance increases your overall security efficacy, and can even successfully block an attack when one layer of security misses. — Corey Nachreiner, CISSP (@SecAdept)
Mining the alphabet soup for what matters part 1 16 Mar 2021, 4:18 pm
NETWORK SECURITY: MINING THE ALPHABET SOUP FOR WHAT MATTERS |
The security industry likes to create acronyms – IAM, UTM, NGFW, MFA, EDR, etc. Perhaps it comes from the general human tendency of wanting to simply define complex topics. In an ever-changing industry, like information security, these acronyms and groupings create major challenges over time. Each year there are new threats, and with that comes more innovation and different approaches to security – all of which we try to initially force into predefined groupings – often diluting the value of the evolving technologies and confusing end-users. One such example is the ongoing attempt to force network security platforms into two distinct groups: Next-Generation Firewall (NGFW) and Unified Threat Management (UTM) appliances. The confusion between the two has become so apparent that analysts at last year’s Gartner’s Security and Risk Management Summit held a roundtable discussion on the very topic. The fact is that most end customers just want good security that solves their network security threats – they care less about NGFW and UTM. Today, I hope to both clear up some of that confusion, and share some data that quantitatively illustrates why UTM protections measurably increase your security efficacy.
UTM VS. NGFW; WHAT’S THE DIFFERENCE?
At one point in time, when analysts first defined these two product segments, they had clear feature delineations in mind. At the highest level, NGFW appliances were firewalls with Intrusion prevention systems (IPS) and application control, whereas UTM appliances were firewalls with IPS, antivirus (AV), URL filtering, and anti-spam capabilities. However, over time both markets have organically evolved and changed. Now both solutions share a similar core set of capabilities. For instance, some NGFW solutions have added new security controls (like malware detection), which used to fall into the UTM camp. Meanwhile, UTMs have adopted all of the security features that helped define the NGFW market—such as application control—and have even added additional new security services to the mix.
This melding of feature sets between NGFW and UTM has made it a bit more difficult to differentiate products, but I think one high level description holds true. UTM solutions focus on unifying as many security controls as possible in one place, making them easier and more cost effective to manage, whereas NGFW solutions focus on only consolidating a limited subset of controls; specifically, ones that make the most sense in certain use cases, such as in a big data center environment. In plain English, UTM solutions tend to include more types of security controls than NGFWs.
HOW LAYERED UTM SECURITY IMPROVES OVERALL DEFENSE
In essence, UTM’s core value proposition is that it combines many security controls in one place, increasing your overall security efficacy, and making layered security attainable for some organizations that couldn’t implement it otherwise. To really appreciate this, you need to understand why layered security improves your overall defense efficacy.
Ultimately, there are two reasons UTM layered security offers the best defense:
- No single security control is infallible – History has proven that information security is a constant arms race. The good guys invent a new security control that blocks an attack at first, but the bad guys react and find new ways to evade those defenses. Antivirus (AV) is a great example of this. The industry started with signature-based solutions that originally did a good job, but eventually the bad guys evolved, and reacted with new evasion techniques that bypassed reactive signature-based solutions. Today, we have more advanced, behavioral-based AV solutions, but already attackers are exploring ways to trick these new solutions. The point is, no matter how great a security control might seem, attackers will find ways around it, which is why it’s important to have the additional layers of security a UTM appliance provides to pick up the slack.
- There are different stages to a modern, blended attacks – You can break down modern network attacks into multiple stages. For example, the initial attack delivery, the exploit portion of the attack, the payload or malware delivery, the call home to the attacker, and so on. Security experts often refer to these stages as the Kill Chain. The importance of these stages is twofold; First, each stage is an additional opportunity for you to catch the attack. If you miss the first stage, you might still stop the second. Also, each of these stages requires a different type of defense. For instance, IPS isn’t intended to catch malware, but rather block software exploits. WatchGuard’s UTM appliances break the Kill Chain by incorporating all the different types of defenses necessary for each stage of an attack, and by layering them together so that a miss at one stage doesn’t rule out a block at another stage. Simply put, the more stages of an attack you protect against, the more effective your overall defense is, even when new threats bypass one defense.
At WatchGuard we care less about what you call what we do – UTM, multi-layered security, NGFW – we care more for the fact that we have created a mechanism to catch all the various stages of a modern network attack, and by layering these protections together, we give you multiple opportunities to block the threat even when one defense fails.
If you have any questions, please feel free to contact us.
Trying on technology 16 Mar 2021, 4:17 pm
Wearables are quickly becoming a major facet of technology. With integration to other smart devices, wearables are making it possible to easily quantify and monitor our lives. There are a variety of wearables available in the market like fitness bands, smartwatches, and even purses that can charge your smartphone. With all these choices available, it can be difficult to decide what kind of device is best for you.
The simplest wearables are the fitness bands. Last Holiday Season, the Fitbit was the most downloaded app from Apple’s App Store; the argument can be made that fitness bands are the most popular wearable technology. A fitness band is an activity tracker that monitors the distance you walk, calorie consumption, heart rate, and sometimes sleep. This is generally a good way to get introduced to wearables and to try them to your liking.
Smartwatches share many of the same technologies as fitness bands, except they are built to serve more functions. These devices enable users to receive notifications from their smartphones for services such as email, calls, and text. There are also apps created specifically for smartwatches. Microsoft and Apple have released their own flagship smartwatches, made to work seamlessly with their mobile operating systems. Android based smartwatches are also an option for consumers looking to enter the market. We recommend going with the device that will work with your existing devices.
Wearables are not limited to devices that can be worn on your wrist. Companies like Recon have begun to create heads up display devices with various sports applications. Fashion companies like Kate Spade and Everpurse have created purses with charging ports for smartphones. The potential for wearables are endless.
If you have any questions, please feel free to contact us.
My mac has a virus, and so does my thermostat! 16 Mar 2021, 4:16 pm
Many computer users are familiar with the dangers of PCs becoming infected by malicious software. In a past post, we described the different types of infections we commonly see. http://www.flashtech.com/portfolio-view/virus-adware-spyware-and-malware-removal/ We are often asked if devices running operating systems other than Windows are susceptible to malware, as well. In short, the answer to this question is yes.
Infected OS X users are often surprised when their device has a virus. Malware is not limited to PCs. Usually at the time of the malware’s creation, hackers create them based on vulnerabilities within the operating system. Apple, Linux, Chrome/Android and PC made computers, laptops, tablets and smartphones are often updated to patch such security vulnerabilities.
Contrary to popular belief, “computers” are not the only devices that are susceptible to malware. Devices that can become infected include, but are not limited to, wireless routers, home automation devices, smartphones, and yes, thermostats. The reason for this is because these devices have an operating system and are capable executing software. Anything that has an operating system can become infected.
To prevent these devices from becoming infected with malware, it is important to implement good computing practices. Examples of good computing practices are enabling security where possible, using a secure password, and keeping devices up-to-date. Many computer users are familiar with updating their computer’s operating system, but many do not realize that routers, media servers and other devices also have updates that should be applied to minimize the chance of an infection.
If you have any questions, please feel free to contact us.
ABCS OF USB 16 Mar 2021, 4:14 pm
USB, or Universal Serial Bus, is the most common way to connect devices to computers. Because it allows for many computer peripherals to be connected using a standardized form factor, USB quickly gained popularity. Over the course of USB’s evolution, it has been implemented through multiple iterations and form factors.
The most common form factor of USB is type A. This is the type of connection you would see on the back of your computer. USB type B is commonly used to connect printers to computers. Cellphones are commonly found with a micro USB type B connection. Usually, these connections have a single orientation, allowing only one way to connect devices to machines.
The first release of USB is known as USB 1.0, or Low Bandwidth, was released in 1996. Common iterations of USB that we see in computers today are 2.0 and 3.0, known as High Speed and SuperSpeed, respectively. The most recent iteration of USB is 3.1, or SuperSpeed+, whose speed reaches 10 Gbits/s. USB 3.1 devices are compatible with computers that have older USB ports, but connect at the slower speeds.
USB type C was developed alongside USB 3.1. USB type C is considered a completely different technology. The most obvious difference between USB type A and USB type C is the form factor. USB C does not have an up or down orientation, it can be connected either way. Another feature that makes USB type C unique is, in addition to carrying power and data, it natively carries video and audio signals as well. USB 1, 2, and 3 devices will work with USB type C port with the correct connectors.
USB continues to be a popular technology for connecting peripherals to computers because of its versatility. It has evolved from a slow simple technology to a fast universal technology. The introduction of USB 3.1 and USB type C further reinforces the universal acceptance of USB.
If you have any questions, please feel free to contact us.
Which cable do I need? 16 Mar 2021, 4:14 pm
A question we are often asked is if there is a cable that will perform a particular function. The answer to this question depends less on the cable and more on the interfaces, or ports, of the devices. Compatibility of interfaces is the determining factor when choosing a cable. The most popular types of ports are network, I/O data, and video.
The first thing is to properly identify the interfaces or ports. The most common way ports are identified is visually. Most ports will have a symbol or a label near it. In some operating systems, it is possible to look up the available interfaces on the computer. It is important to know the interfaces on the device you are trying to connect, and the port you are connecting on the computer.
The second thing to know is the function of the port or interface. Just because something fits, doesn’t mean it’s going to work. You have to make sure the port or interface will support the function you are trying to achieve. For example a printer may have 2 USB ports, but they do not serve the same function. One USB port is a data port to connect the printer to the computer and the other USB port allows you to connect removable storage to print directly without a computer. They are both USB ports but function differently.
Some interfaces are mixed use and have multi-functions. For example, the new USB-C interface can be used for data, networking, sound, and video. This interface can be considered the Swiss Army Knife of interfaces. Also these interfaces are backwards compatible. This means new devices will work on older computers.
Finally, while there are cables that may allow devices to connect to one another, that does not guarantee it will perform the desired function. The communication between the devices has to be consistent. For example, a computer that outputs an analog video signal would not be able to communicate with a monitor that only accepts a digital input signal. Any cable can be created to fit, but function requires much more than a connection between devices (usually through some type of converter).
Ultimately, the choice of cables is dependent on the ports of the devices the customer wishes to connect and the compatibility of those ports. There are many ways to identify interfaces. We suggest taking pictures of the interfaces on the devices, so we can identify the proper cable visually.
If you have any questions, please feel free to contact us.
How does email work? 16 Mar 2021, 4:12 pm
Email is something that everybody uses but most people don’t realize how it works. There are different email protocols that determine how email is downloaded, stored and accessed.
There are 3 types of email protocols: POP3, IMAP and SMTP. POP3 and IMAP are protocols that retrieve emails from a mail server, and SMTP is a protocol that sends emails from one email server to another.
POP3 (Post Office Protocol) allows you to download emails to a single computer. POP3 is designed to delete the emails from the server after the user has downloaded it. If you only access emails from one location, POP3 is a good choice. There are options to leave email on the server, but you should check with your email service provider to see if the option is available and for how long the email may be stored.
IMAP (Internet Message Access Protocol) is similar to POP3 because it allows you to access your email from the email server but the emails are stored on the server and not deleted when downloaded. IMAP also allows you to view your emails on different computers and devices from any location simultaneously. If you view an email, move it to a different folder or make any other changes, those changes will be made on the server and will show on any device that is used to view the email in real time. You should check with your email service provide to see how long email will be stored.
SMTP (Simple Mail Transfer Protocol) is used to send emails from one email server to another email server. The emails can then be retrieved with POP3 or IMAP. No matter what email program is being used, SMTP will be the protocol that sends the email over the internet, between servers.
Most email providers, such as Gmail or Yahoo, have customers access their email via IMAP. This is the reason users are able to check their email on different devices, at the same time, if needed. Some companies have a server that will only allow the user to open their emails at that location with a specific email client such as Outlook.
When setting up an email, it is important to know what type of email and what type of protocol will be used so the server can download and store the email properly.
If you have any questions, please feel free to contact us.
Why do I need a secure password? 16 Mar 2021, 4:11 pm
A lot of people have been asking whether or not they need a computer password. A password is always a good idea on any of your devices and accounts. Think about your computer like an apartment building. If somebody gets into the front door, you will still have a lock on your apartment door, keeping them out of your personal area or data. The lock on your apartment door is your password.
Flash Tech recommends having a password that is at least 10 characters long with at least one character being capital letters, numbers and symbols. We would also suggest using memorable phrases or quotes or a mnemonic such as May the Force be with you! MtFbwy1!. This will make it much harder for someone to guess your password or use software to try to crack it. Creating a password this way will also help you remember what it is.
When creating a password, avoid words found in the dictionary, usernames, pet names, family names, addresses and birthdays. These are the most common things that people use for passwords and are the first things hackers will try to use to gain access to your accounts and personal files. The harder it is to guess your password, the longer it will take for someone to crack it.
There are apps and online services that can tell you how strong your password is, suggest how to make it more secure, and how long it could take to crack it. If you are skeptical about using a program or website you have never heard of, Microsoft offers an online strength checker that is said to be completely secure and Macs have the built-in Password Assistant. Also, there are password manager programs such as 1Password, Dashlane and LastPass that allow you to save all of your passwords in one spot while using one master password to be able to access the rest. Using these programs are a good idea if you don’t want to remember several passwords, you would only need to remember the master password to the program which saves all of your other passwords. These programs have apps for your phones and tablets as well. These apps and online checkers are only as secure as the provider. One way to make these more secure is to use 2-step authentication. 2-step authentication is a way to make your accounts more secure by requiring a code from an app on your phone after you put in your password to verify that it is you trying to log in. LastPass and Dashlane have built-in 2-step authentication.
Remember, when creating a password, it is strongly suggested that it is a minimum of 10 characters long. Do not use any personal information and add special characters, punctuation and capital letters to make it as secure as possible. If you have any questions, please contact us.
What is the difference between BIOS and UEFI? 16 Mar 2021, 4:10 pm
They both control the boot process of a computer but work in different ways and provide different options.
BIOS (Basic Input/Output System) is firmware used during the boot process on a PC. BIOS is responsible for the communication between the operating system and the I/O (input/output) devices, such as the keyboard and the monitor. When the computer is powered on, the BIOS performs a Power On Self Test (POST) which checks different hardware to make sure they are working properly. Finally, it looks on the first sector of the hard drive for instructions on how to boot the operating system (OS) and then the OS takes over from there. BIOS will only support MBR partitions with storage restrictions of 2TB.
UEFI (Unified Extensible Firmware Interface) is also firmware used during the boot process but can be used for Mac or PC. UEFI does the same thing as BIOS with a more user-friendly interface, making it easier for the end-user to make changes to the system. UEFI also allows the use of GPT partitions which are able to handle storage capacities up to 8 Zettabytes (ZB) which is equal to 8 billion Terabytes (TB). It also has the ability to boot off of a hard drive that is larger than 2 TB, as long as the motherboard supports it. UEFI stores the startup information in a .efi file instead of on the firmware and stores it in an EFI system partition (ESP) on the hard drive. The .efi file contains the boot loader for the installed operating systems, device drivers that are necessary for the boot process, any system utilities that run before the OS is booted and data/log files. Different than BIOS, UEFI controls the boot process rather than handing it over to the OS.
If you have any questions, feel free to contact us or come into our store to speak to a technician.
How can I use it on a mac and pc? 16 Mar 2021, 4:09 pm
One common question we get asked is, “How can I use my external hard drive to backup and/or transfer files between a Mac and a PC?” Generally, there are 2 ways.
When you format the drive using the FAT file system, the drive will be recognized on all Macs and all PCs. The downside to using FAT is that it will not support any file larger than 4GB.
The other option is to use exFAT. exFAT is the better alternative to FAT, in most cases, because it is able to handle a file larger than 4GB and will work with both Mac and PC. One limitation to exFAT is that it will only work with newer operating systems: OS X 10.6.5 (Snow Leopard) or higher, and Windows Vista and newer.
NOTE: A Mac computer is able to see NTFS partitions. This means that you can view any files from an NTFS hard drive on a Mac, but you will not be able to save or edit the files.
It is important to note that any programs you use will not transfer from one computer to another. If you have files on one computer that require a certain program to view and edit, you will need the same or a compatible program installed on the other computer.
If you have any questions about what the right option for you is, feel free to contact us or come into our store to speak to a technician.